2020 changed the cyber security landscape
2020 was a year of substantial change especially in the space of Distributed Denial of Service (DDoS) attacks, as the world came to terms with the new ways of working and living with Covid-19. Collectively we witnessed the majority of the corporate world forced to stand up an online workforce and a secure digital environment for their staff within a matter of hours or days.
Traditional industries had to adapt and quickly transition to a secure online presence. Industries such as education were quickly moved to a digital learning structure with millions of students now taking classes virtually. Government agencies saw all of their staff transition to working from home and the need to implement secure online processes that had - up until Covid-19 been paper driven or executed in person. Adding to the abnormality of it all, IT or security teams didn’t have any time to test or put in place the necessary security precautions before forcing everyone to work from home.
With the world now more interconnected than ever and the virtual workplace and classrooms being the new normal, it highlighted the vulnerability and therefore opportunities within cyber security. Covid-19 has presented cyber attackers with a larger than ever threat attack surface.
As a company that specialises in Distributed Denial of Service attacks or more commonly known as cyber security attacks, we have seen a shift in sophistication over the last year. As previously mentioned 2020 provided an unprecedented attack surface for cyber criminals opening up a new threat landscape. As the implications of Covid-19 started to sink in, it became very apparent that DDoS attacks had changed and become considerably more sophisticated as cyber criminals adapted to the new online world.
This diagram clearly illustrates the steady rise in the number of attacks we saw over the last six months from November 2020 to now, May 2021.
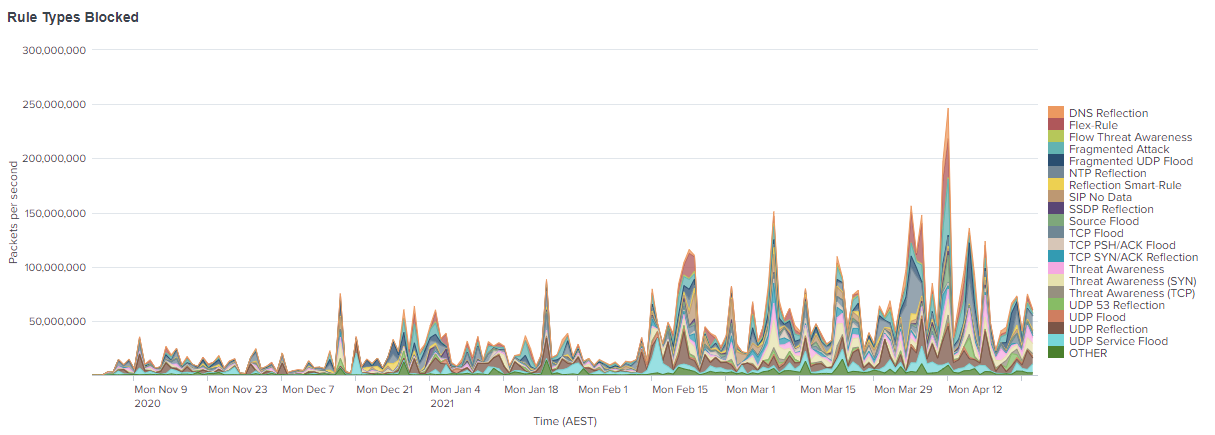
At GSL, we love data, so let's put some tangible figures around that diagram.
That equates to 51,816 attacks in the last year, 4318 attacks in the last month and 142 attacks a day.
One of the changes our security team at Global Secure Layer saw was a considerable shift from single vector attacks to multi vector attacks.
A shift from single vector to multi vector attack
Multi vector attacks occur when cyber criminals try to flood a company's security defences with multiple attack vectors targeting their network, application and data layers. 2020 displayed a greater number of multi vector attacks with attackers using numerous techniques to take servers and networks offline.
Last year highlighted that these coordinated attacks are a huge concern and a very real possibility for organisations. It is no longer enough for these organisations to have a brief understanding of DDoS attacks, it is a necessity that they understand the rate in which they grow in sophistication but also have the ability to mitigate against the most recent and up to date attack vectors. A prime example is being up to date with Zero Day attack vectors and having the right products and capability to mitigate against them effectively before an exploit occurs.
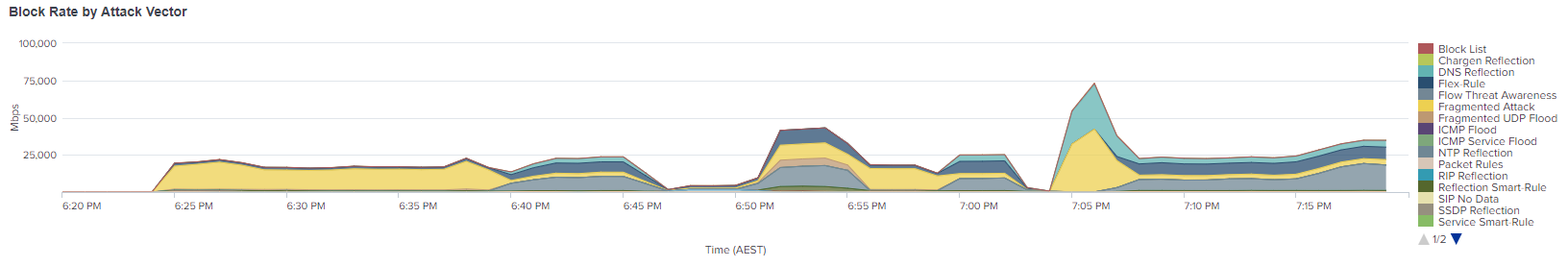
This graph is a perfect example of a sophisticated multi vector attack. It starts off as a single vector attack at the beginning - the yellow, and then quickly moves to a multi vector attack.
Mimicking real traffic
Aside from attackers shifting to a multi vector approach we also saw the mimicking of real traffic become extremely prevalent last year. This was particularly important and caught the attention of our security team as the attack vectors were different to ‘usual DDoS attacks’. Attackers specifically tried to hide their attacks to spoof the targeted organisation’s security defences and come across as real users. Traditional DDoS mitigation is unable to detect the difference between the traffic and as a result can cause downtime for organisations.
Now, it doesn’t just stop with mimicking traffic. These days, people executing the above attacks use the mimicking of real traffic as a ‘smoke and mirrors’ strategy. They target one aspect of the network to draw the network and security team to focus on a particular problem while they attack a different part. Mimicking real traffic is usually never the end goal for the attackers, nine times out of ten attacking another part of the network was their intention, they just used the ‘smoke and mirrors’ act to divert resources.
A rise in DDoS for ransom attacks
DDoS for ransom attackers have caught the attention of media, government agencies as well as large organisations around the world particularly in 2020. Their ransom-based DDoS attacks are best known for targeting companies within various industries, sizes and locations with the threat of taking their network, website or application offline for a period of time unless a ransom payment is made to the cyber crime group.
Over the last year, cyber criminals have used tactics such as a shift to multi vector attacks and mimicking traffic, just to name a few as a way to execute DDoS for ransom attacks.
In the last 12 months, organisations across the globe have been targeted specifically by a group of cyber criminals. These targeted organisations receive extortion messages that promise to launch an attack if the chosen organisation does not pay the ransom amount in bitcoin.
Our in-house DDoS mitigation capabilities have the ability to not only mitigate against the most sophisticated and recent attack vectors but also learn from previous attacks allowing it to grasp sophisticated patterns and protect against them.
Our case study featuring Net Virtue dives into these DDoS for ransom attacks specifically and looks into things such as attack specifications, attack source ports and the solution we, at Global Secure Layer provided.
This last year has set a precedent in the cyber security space and highlighted the vulnerabilities organisations’ are exposed to. Whether that be a multinational, government agency or SME, it has demonstrated the absolute need for these companies to have both a proactive and reactive DDoS mitigation solution. This online landscape we are now all exposed to is the new norm and as a corporate world, DDoS mitigation needs to be at the top of the agenda for all online businesses.
If you would like to talk to our team about DDoS mitigation services, please don't hesitate to get in touch.


