Case Study:
Net Virtue
About Net Virtue
Net Virtue is a leading web solution provider delivering affordable and reliable services to clients all over the country. Founded in 2011, the company is 100% Australian owned and operated. Net Virtue provides a vast range of services including web hosting, virtual private servers, dedicated servers and colocation within the Australian market.
Net Virtue needed a fast, reliable and secure solution for a DDoS for ransom attack they received in September 2020.

"The attack profile was so large our existing DDoS mitigation platform was entirely overwhelmed and we needed a DDoS partner urgently that would scrub the traffic and bring our network back online."
Challenge
DDoS for ransom attack
Over the last few months Global Secure Layer (GSL) has seen a substantial rise in the number of DDoS for ransom attacks, also more commonly known as cybersecurity attacks. Organisations across the globe have been targeted specifically by a group of cybercriminals.
DDoS for ransom attackers have caught the attention of media, government agencies as well as large organisations around the world particularly in 2020. Their ransom-based DDoS attacks are best known for targeting companies within various industries, sizes and locations with the threat of taking their network, website or application offline for a period of time unless a ransom payment is made to the cybercrime group.
These targeted organisations receive extortion messages that promise to launch an attack if the chosen organisation does not pay the ransom amount in bitcoin.
Attack Specifications
Distributed denial-of-service (DDoS) attacks are one of the most complex security challenges of the modern internet. The impact these attacks can have on an organisation can be crippling if not mitigated quickly and efficiently.
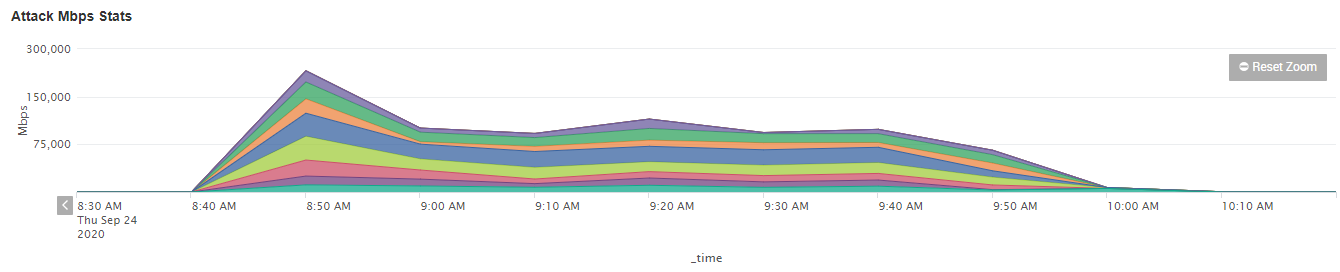
The below graph displays the first attack deployed by the DDoS for ransom attackers targeting Net Virtue that continued for two days. Each colour on the graph represents a different target IP address. The below illustration is of particular interest as it is unprecedented for there to be an entire /24 being under attack at the same time. To put that into tangible figures, this is up to 254 IPs at once. Each IP that was targeted was small, but this was deliberate as they were attempting to bypass traditional mitigation measures. The total sum of the attacks peaked out just below 300Gbit/s.
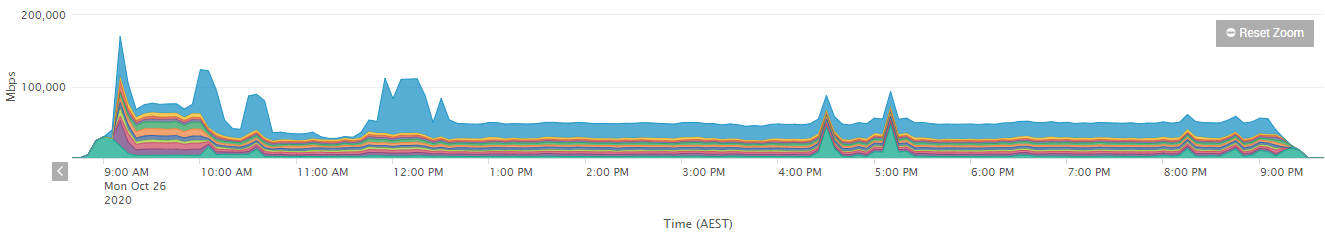
The second graph illustrates another wave that occurred a month later and lasted an entire day rather than a few hours. Taking particular note of the time the attacks started and ended - with the intention of taking the network down for the entire ‘work’ day. DDoS for ransom attackers often target an organisation more than once allowing for time to pass between attacks. This is in order to see whether the organisation has deployed a mitigation solution that is robust enough and working 24/7.
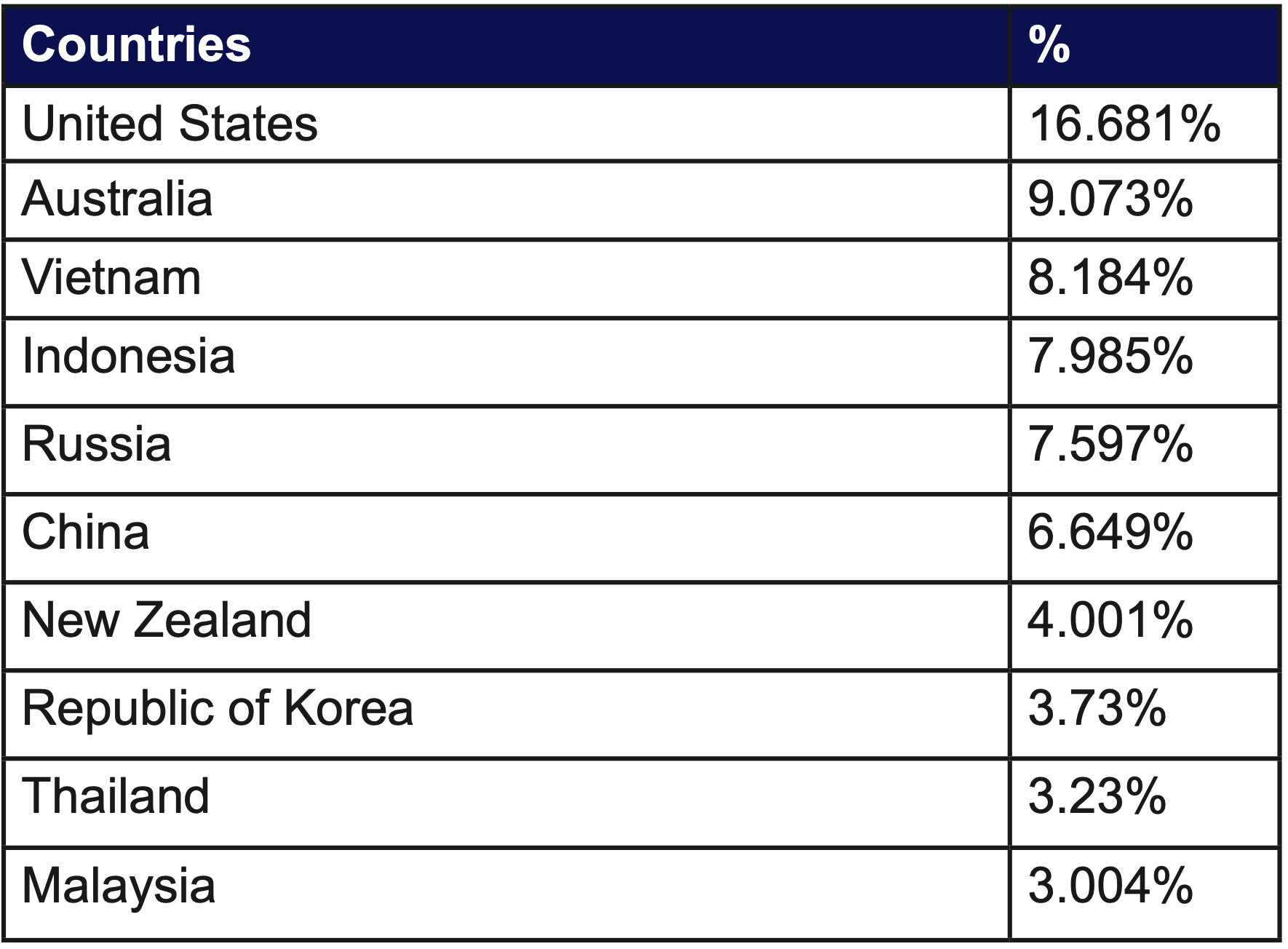
Countries
The table below illustrates the widespread nature of where the attack traffic originated from, in particular the substantial amount of traffic originating from Australia and New Zealand. This brings to attention the concern that these DDoS for ransom attacks are building localised botnets. In the coming months, these localised botnets will cause unparalleled damage on unprotected equipment in Oceania.
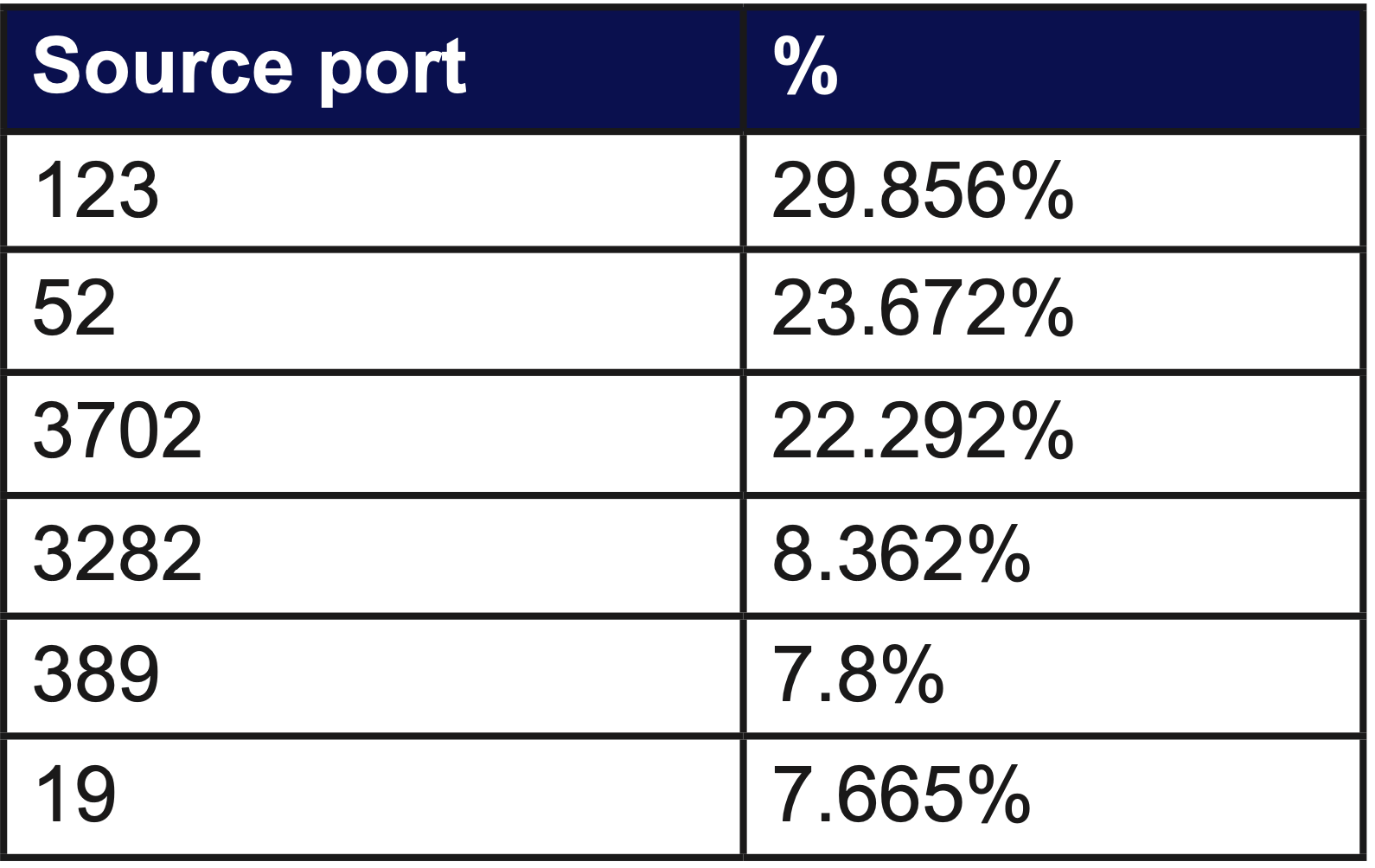
Attack source ports
Cybercriminals can, and often do, dynamically change their attack vectors in order to defeat traditional mitigation defences. This was no exception in the attacks targeting Net Virtue. Watching the events unfold, one might say this was similar to a boxing match. As GSL mitigated against the attacks each time, the threat based actors would try a different attack vector attempting to ‘outwit’ their opponent.
GSL’s protection and security mitigation experts surgically removed the traffic before it reached internal systems. The mitigation systems Global Secure Layer had implemented were able to learn from previous attacks allowing it to grasp sophisticated patterns and protect against them.
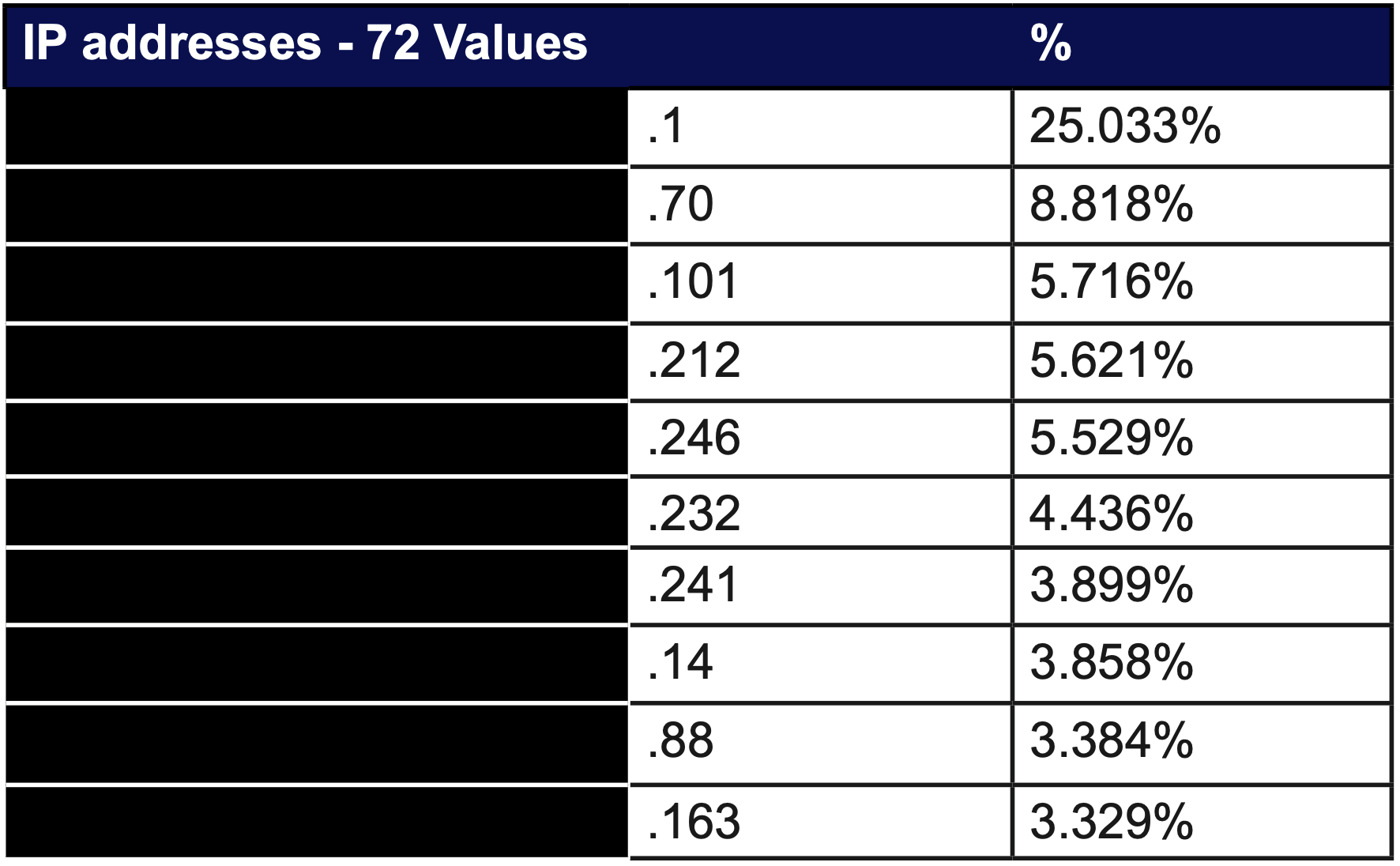
IP addresses
Particular interest has to be shown towards the number of destination IP addresses (72) that were attacked simultaneously during the second attack. Each destination IP was targeted with low volumes of traffic
Choosing GSL
As a company, Global Secure Layer assisted Net Virtue in seamlessly transitioning over to their global Anycast DDoS mitigation platform within a matter of minutes after they came under attack back in September 2020.
The DDoS mitigation solution provided by Global Secure Layer was online within minutes once direct connectivity was established between both networks. Due to the high profile DDoS for ransom messages received, Net Virtue was set up on GSL’s highest protection platform. This included:
- Global Mitigation Announcements (500Gbit+)
- Direct connection to GSL’s 100Gbit Sydney Arista core
- Custom mitigation rules applied (fine tuned for Net Virtue’s hosting business)
Throughout the week that Net Virtue was under attack, the security operations team at Global Secure Layer worked directly with the team at Net Virtue to defend against the constant and ever evolving DDoS attacks. This involved deploying additional custom mitigation rules, restructuring BGP announcements to increase mitigation capacity and hardening firewalls.
This attack has now been fed into Global Secure Layer’s global mitigation AI based grey list. The results are being analysed by our security team and will be deployed onto our global network in order to protect all of our customers against the specific attack vectors Net Virtue faced.
Results
“From the moment GSL put us on their DDoS protection system, within minutes our network was being protected from the ransom attackers, said Daniel."
"Not only did the team from GSL react within minutes from us contacting them, the level of technical support we received was second-to-none."
“As a company, we had complete confidence in their protection as we had witnessed first hand its capabilities, so when the second round of attacks started we knew our network would be protected.”

"The transition to GSL has given us the confidence to know our network is protected against any future DDoS attacks.”


