WSD DDoS Vector in the Wild
You may have heard or seen the acronym WSD being used on your computer and wondered what it was and why it was important? Well, this blog is going to explain the importance of WSD and how it is relevant in the landscape of security attacks.
What is WSD?
Web Services for Devices (WSD) is a Microsoft API to enable programming connections to web service enabled devices, such as printers, scanners and file shares, easing customer device connectivity. This communicates over source port 3702 and until recently hasn’t been seen under active exploitation for use in DDoS attacks.
The problem with WSD is that requests to it can be spoofed, in turn, an exploited server can be used as a “reflector” to unknowingly send responses to a victim server/network and overwhelm its bandwidth capacity.
How is it possible?
Web Services for Devices was never designed to be open to the public internet, it was developed for ease of use and to be used inside a local LAN network. Unfortunately, manufacturers of WSD enabled devices (printers, scanners, IOT devices) pushed out improper implementation of WSD and exposed hundreds of thousands of devices to easy exploitation and in turn DDoS reflectors.
A real-world example of a WSD attack
In late 2019, attackers started to exploit the recent (at the time) WSD vector against our gaming and business clients. In particular, targeting services that they could monitor for adverse effects in real-time.
The attack was picked up and mitigated by our DDoS mitigation devices in Los Angeles, Sydney and Singapore.
Why are attackers using WSD?
In short, it’s due to the amplification possibilities of WSD, the vector has been noted to be the 4th highest amplification method at (15,300%), trailing closely behind more traditional methods (DNS, NTP & LDAP).
Amplification attacks use a small amount of traffic from a source that is then amplified via servers and targeted towards a victim’s IP. These requests start small and turn into large attacks. This is concerning for all industries because even a small 10-byte request from a single server would be amplified into a ~153Kb response targeted towards the victim. This is exponentially increased as more servers are exploited and combined to target a single victim.
WSD attack size
While the example given was only small in the grand scheme of DDoS attacks, peaking at 75Gbit/s and 8,580,000PPS it shows the vector is now fully in the wild and we expect to see more of the attack in the near future.

WSD Attack Vector reported by GSL Mitigation Devices
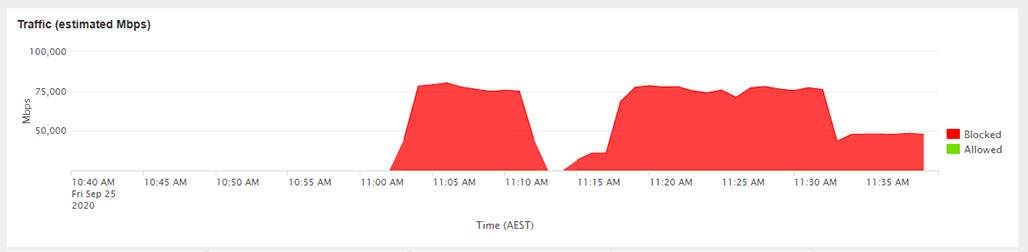
WSD Attack Vector Size
What is Global Secure Layer doing about it?
Our real-time protection service automatically analysed, scrubbed and flagged the new attack vector for further review by our mitigation team. Since then, we have already developed and released a more specific custom rule to cover the new vector. The real-world WSD attack spoken about earlier was detected and mitigated using this new rule and saw no issue to the client’s services targeted.
Author: Callum, Chief Operating Officer at GSL
If you would like to talk to our team about DDoS mitigation, please don't hesitate to get in touch.


