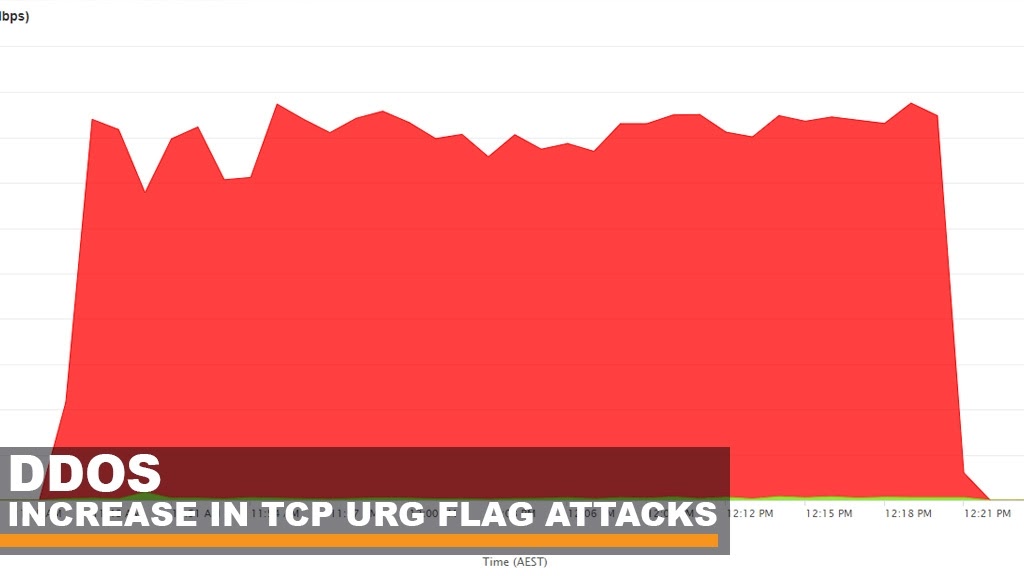
DDoS increase in TCP URG Flag Attacks
As we come to the end of September, GSL has seen a recent rise in TCP flood attacks against services under the Global Secure Layer DDoS umbrella. In particular, these attacks have been focused on using deprecated TCP Flag “URG”. Similar to most attacks the URG packet is designed to disrupt network activity by saturating the bandwidth and resources of its selected target.
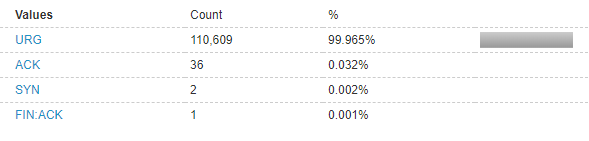
The URG flag is used to inform the receiving system that the data contained in a certain segment of the payload is urgent and should be prioritised over other packets (hence the name URG). The URG flag isn't employed much by modern protocol and has been less widely used in the last decade. Some legacy systems still use the flag, however, it is not common to see in network analysis. Due to its lack of use, it certainly raised some red flags the moment it entered our global network.
Technical Analysis
The URG flag attack itself is fairly basic in comparison to the other attacks we see, and is nothing compared to some SRCDS vectors we come across. The reason the URG flag attack is less eventful is because it doesn’t contain anything “interesting” in the payload, except of course the TCP flag URG. Looking over the attack it is a typical TCP flood coming from >50,000 IPs and random source ports. The attack was fairly sizeable, at its peak reaching ~10m PPS at 21Gbit/s. In a typical mitigation environment, this can be difficult to scrub against - as the packets at first glance appear legitimate.
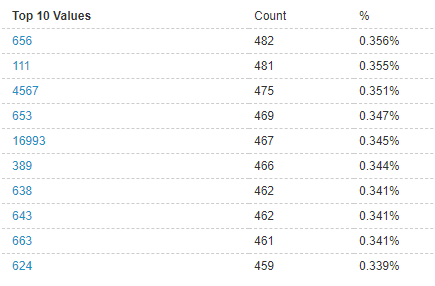
Source ports
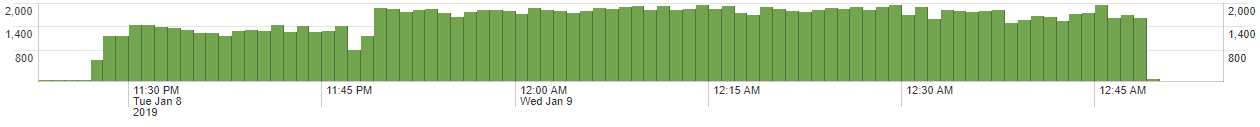
DDoS event graph
Smart rule graph
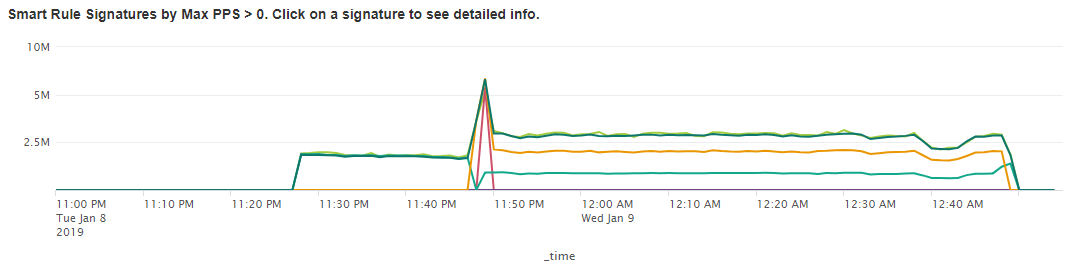
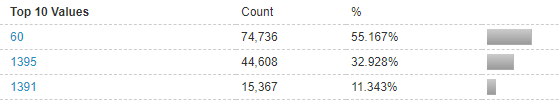
Using our mitigation infrastructure Global Secure Layer is able to inspect every packet in real-time, determine key features of a TCP flood and begin mitigation within 1 second of the attack starting. The main factors we were able to pick up on were the high time to live (TTL) >224 and a consistent packet length. TTL is the number of hops that a packet is permitted to travel before being discarded by a router. The attacker will often set this to a high number to ensure the DDoS reaches its target without being dropped by a router along the way.
High TTL
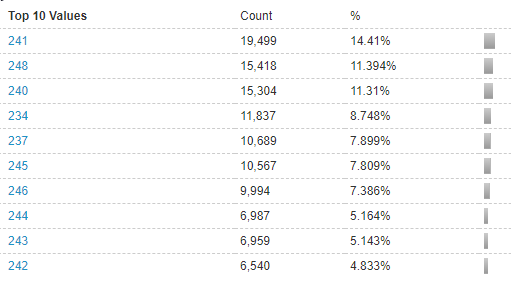
Packet length
Flags decoded
Author: Callum, Chief Operating Officer at GSL
If you have any questions about our DDoS protection or other services, don’t hesitate to get in contact with the GSL team.


